security – 2 – modules
May 28, 2015 | By admin |
Multiple Modules
The Secrata Platform offers security hardening for data and workflows through multiple modules. Each module provides the building blocks for the enterprise to secure and control data across its infrastructure and wide area internet regardless of the device or system being used.
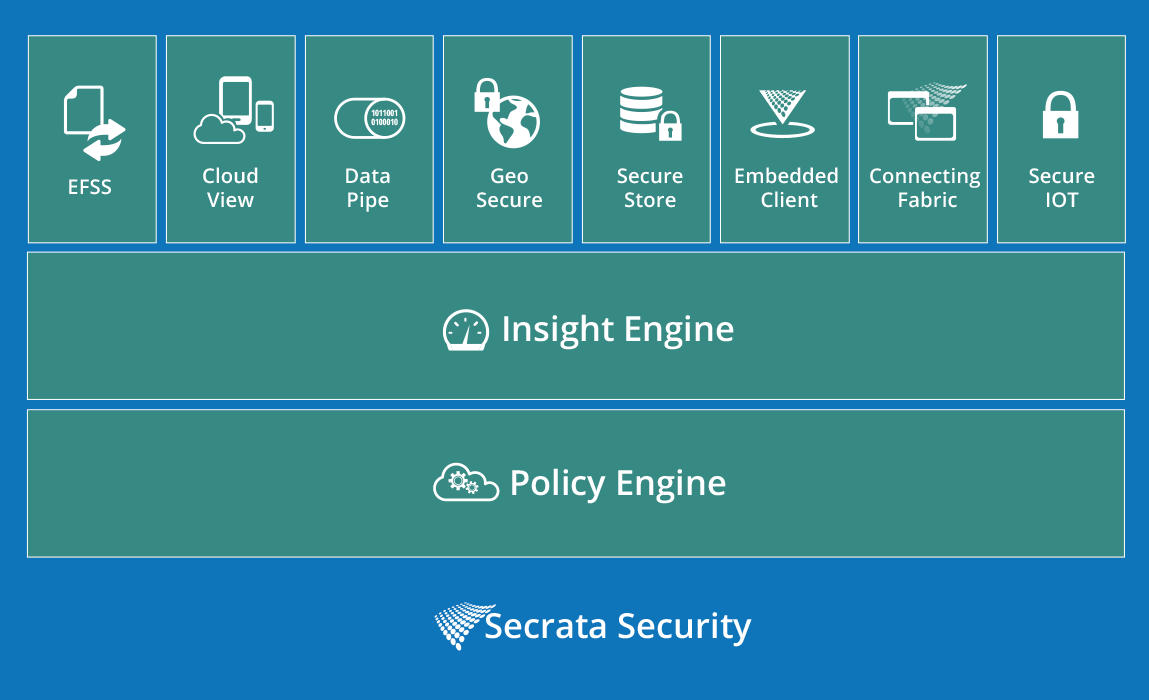
EFSS
EFSS™ is the most secure way to move and manage files across content locations (data stores). This Secrata module ensures full control and visibility for IT, and provides ease of use for employees. Secrata uses workspaces to help the user manage their files. An integrated messaging platform provides a way to securely collaborate and annotate documents. Secrata is easily integrated into existing workflows to drive adoption and extend corporate assets. IT can control where files can reside and be sent, using a powerful policy engine. Secrata is elegantly simple to use, and powerfully secure.
CloudView
CloudView™ creates a unified user experience across file locations. This Secrata module allows the enterprise to securely register content where it lives… no need to aggregate files into a single location or cloud vendor. Cloud View extracts metadata to securely and easily find and manage files no matter where they reside. Files are not dumbly replicated but are securely made available to access or share from any data store. IT remains in control and the user remains productive.
DataPipe
DataPipe™ is the most secure way to move data between machine end-points. This Secrata module enables secure optimized transfer of any type of data to a remote location. Now, POS transactions, medical device data, or any point-to-point data transfer can have unmatched security that goes far beyond encryption.
GeoSecure
GeoSecure™ adds a new dimension to data security—location. This Secrata module uses GPS and IP geolocation to give you a powerful way to secure data based on a user’s location. Administrators can restrict access to files and data in a Secrata Workspace when access is attempted from a restricted location. Now, you can ensure that sensitive assets cannot be downloaded, shared, or even viewed from dangerous locations such as foreign countries, unsecure WiFi networks, or outside a company location.
StoreSecure
StoreSecure™ allows the enterprise to shred and encrypt files at rest. This Secrata module goes beyond encryption and introduces shredding with unique encryption keys for each resulting shred. The enterprise now has a way to further mitigate the risks to its file assets.
Embedded Client
The Embedded Client™ allows Secrata to be integrated into devices and applications through the inclusion of a library containing a micro client for Secrata. This micro client provides all the secure access and transfer of data like a full client, but with a reduced footprint and entirely programmatic control.
Connecting Fabric
Integration with third-party applications is also secure using the Connecting Fabric™ integration module and software APIs. Connecting Fabric allows integration with Secrata, CloudView, or other Secrata modules, free from the threat of malware, both to the enterprise and to the external integration platform.
SecureIOT
As connectivity expands with the introduction of IPV6, SecureIOT enables secure transfer from emerging categories of network enabled devices. By shredding and encrypting data between these devices, your Internet of things can expand with unmatched security.
Insight Engine
The Insight Engine™ module provides administrators and managers with visibility into the files and data being sent through the Secrata. By visualizing the flow of data using the metadata collected by the clients and server, administrators can see where data is being used and who has been accessing it, giving them stronger control over their corporate data.
Policy Engine
The Policy Engine™ module is a secure console that allows enterprise administrators to roll out, manage, and ensure compliance with enterprise data security policies. Policies may be adjusted by user, device, or service, and files may be coded with metadata that aligns with security policies covering access and sharing privileges. The Policy Engine also fully logs all data transfer, whether machine-to-machine or user-initiated. Auditing by service, device, user, workspace, and file is supported, and reporting data may be exported to other applications to mine system and service intelligence.

